Guide
History of Bug Bounties
A quick guide on the history of bug bounties, from 1995 to present.
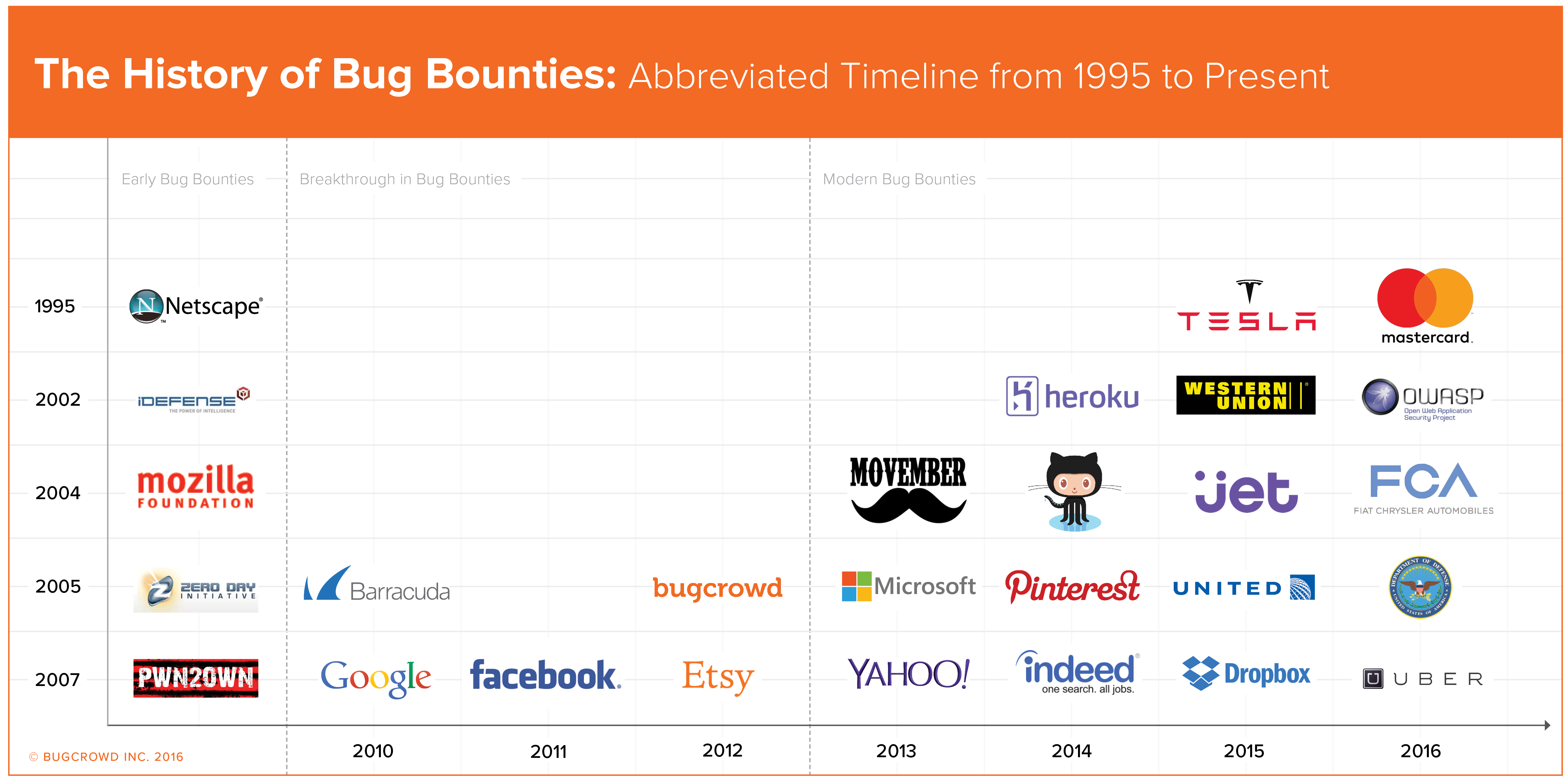
Early Bug Bounties
The first bug bounty program was created by Jarrett Ridlonghafer, a Technical Support Engineer at Netscape in late 1995. This first bug bounty program was used to find bugs in Netscape’s Navigator 2.0 Internet Browser. The idea of this first bug bounty program was to incentivize people to provide feedback on the Netscape Navigator 2.0 by providing cash rewards to anyone who found bugs in their software. Although Netscape was successful in creating the first bug bounty, and the program is noted as one of Netscape’s biggest successes, the bug bounty program did not spread quickly among other software companies initially.
The security company IDefense, later acquired by VeriSign, was next to start a bug bounty program, creating a middleman approach by providing cash prizes to researchers who reported bugs in software and report it directly to them.
Nine years after the first bug bounty program was introduced, The Mozilla Foundation created a bug bounty program in 2004. This program included Firefox and offered researchers cash payment for any critical vulnerabilities they found in the software. Mozilla’s bug bounty program is still going today and covers almost all Mozilla’s products and has paid out over $1 million.
Shortly thereafter, TippingPoint introduced their bug bounty program called the Zero Day Initiative (ZDI) offering rewards to ‘reputable hackers.’
Another major event that defines the history of bug bounties is the Pwn2own hacking competition that takes place every year at CanSecWest security conference. This hacking competition was started in 2007 to find security bugs in Mac’s OSX. Today the competition includes awards to anyone who hacks a phone or web browser with a $15,000 cash prize. Since its creation, Pwn2Own has gained significant media attention and has raised awareness about security vulnerabilities.
The Breakthrough in Bug Bounties:
A real breakthrough in the history of bug bounty programs came in 2010 with the introduction of Google’s Vulnerability Reward Program (VRP) for the company’s web applications. Google introduced this year-round bug bounty program along with a similar program for their open-source Chromium project. Since their launch, Google has paid out over $6 million.
Also in 2010, security and data storage company, Barracuda Networks, launched a bug bounty program. The creation of Barracuda’s bug bounty program pushed the computer security industry to continually deliver high-quality security products and was the first security vendor to offer such a program. Today they reward researchers between $500 and $3133.7, depending on the severity of the vulnerability.
Facebook's bug bounty program launched in 2011 and changed the face of the bug bounty economy. As one of the highest esteemed bounty programs, the Facebook Bug Bounty Program covers all the services owned by Facebook including Instagram and has paid more than $4.3 million to researchers around the globe.
The next big company to start a bounty program was Microsoft, in November 2013, initiating their Mitigation Bypass Bounty and the Bounty for Defense. Since then they have expanded their programs and to date have paid out over $500K.
The Modern Bug Bounty
Bug bounties, although incredibly useful and efficient, can be difficult for organizations without the necessary infrastructure or resources to organize, launch and manage them. By working as a middleman between organizations’ security or development teams and the security researcher community, 3rd party platforms, such as Bugcrowd's Crowdcontrol, make bug bounties more efficient and accessible.
Today, these bug bounty platforms allow organizations outside of Silicon Valley tech companies to run both public and private bug bounty programs, including more traditional Financial Services organizations such as Western Union who launched their program in 2013 with Bugcrowd.
Even non-profits such as Movember, a charity foundation focusing on men’s health, were able to tap into the bug bounty economy starting in 2013, offering ‘charity points’ for valid submissions. Another non-profit, the cybersecurity accreditation organization (ISC)2, introduced bug hunting as an accepted way for members to maintain their accreditation in 2014.
Bugcrowd alone has run over 300 programs to date for a myriad of companies, including Heroku, Indeed.com, Pinterest, and Jet.com. Read Bugcrowd’s Second Annual State of Bug Bounty Report for a comprehensive look at organizations running bug bounty programs.
High Profile Programs in Recent Bug Bounty History
With increasing popularity and accessibility, bug bounties can be utilized for technologies other than just websites and web facing applications, such as mobile, IoT and even cars. The first major car manufacturer to adopt the model, Tesla Motors, generated immense media attention in mid-2015 as the first organized car hacking bug bounty program and now offers awards up to $10K.
In May 2015, United Airlines announced their bug bounty program offering airline miles for valid submissions. The program has shelled out nearly 2 million airline miles as of the beginning of 2016 and is paving the way for large corporations to work with the security researcher community. Similarly, in early 2016, GM launched their vulnerability disclosure program, receiving mixed reviews, and Uber launched their bounty program with a ‘treasure map.’ Both of these programs signal continued adoption and the work that must be done to support the continued alignment between organizations and the security research community.
Perhaps the biggest news hitting the bug bounty ecosystem in the last year came from an unexpected source - the United States Department of Defense. During the 2016 RSA Conference, the DoD announced their bounty program, 'Hack the Pentagon,' which kicked off a few months later as a 20-day trial program.
The bug bounty economy continues to evolve from its’ beginnings in 1995 as more organizations adopt the model, and more security researchers participate in the programs. Want to learn more about the bug bounty economy?
Additional Resources:
- http://www.computerweekly.com/news/2240061418/iDefense-doubles-bug-bounty
- http://www.cnet.com/news/offering-a-bounty-for-security-bugs/
- https://en.wikipedia.org/wiki/Bug_bounty_program
- http://www.wired.com/2013/06/microsoft-bug-bounty-program/
- http://www.pcworld.com/article/238120/bug_bounties_why_paying_hackers_makes_you_safer.html


